Unlock mobile credentials with a software-only upgrade
Provide tenants, employees, and members with a single mobile credential to unlock doors across multiple facilities. Keep your proximity card readers installed, no new reader hardware is necessary.

Compatible with major access control systems
Sentry Interactive’s open and interoperable readerless mobile credential software integrates with all major pre-installed and new physical access control systems (PACS), without having to install new readers. Our mobile credentials don’t replace your system, they enhance it.


















The mobile becomes the smartest and most secure reader and credential
The smartphone is the most advanced door reader out there. Our readerless mobile access credential software can simply be updated to provide the highest levels of access control security. No new access control readers are required to be installed.
Achieve an ROI by saving on new reader hardware replacement costs
Our mobile credential software compliments your legacy proximity card reader system. No access control readers are required to be replaced, our software simply adds the option of NFC mobile access, alongside keycard access.

No disruption to existing access control system infrastructure
Our smart access tiles that require no batteries or power are simply applied next to doors and linked with the cloud via the QR code. Setup is remote to enable, fast, reliable, and secure smartphone NFC door entry in no time, without compromising security.

Enhance your access control with a readerless upgrade to mobile credentials
Enjoy a cost-effective software based transition to advanced readerless NFC mobile access, without any disruption to your legacy access control system.
Readerless
Mobile credentials don’t require reader hardware to operate, therefore no reader hardware upgrades or rip and replace is necessary to integrate with your legacy access control system.
Interoperable
Our open SDK is designed to integrate with multiple major access control systems in addition to a portfolio of third-party space management and tenant experience applications.
Scalable
Mobile credentials can be setup and rolled out remotely in minutes and not days, with no disruption to existing access control system infrastructure.
Secure
The only NIST compliant NFC mobile access credential SDK that delivers the highest banking level encryption. Time, geofence and IP restrictions available.
Enhance your apps existing features with integrated mobile credentials
Our SDK integrates with third party applications to manage all buildings effortlessly. No matter the size or sector; from building and facilities management apps, to club, hospitatlity, and coworking and visitor management apps, our SDK increase its capabilities to mobile access credentials.
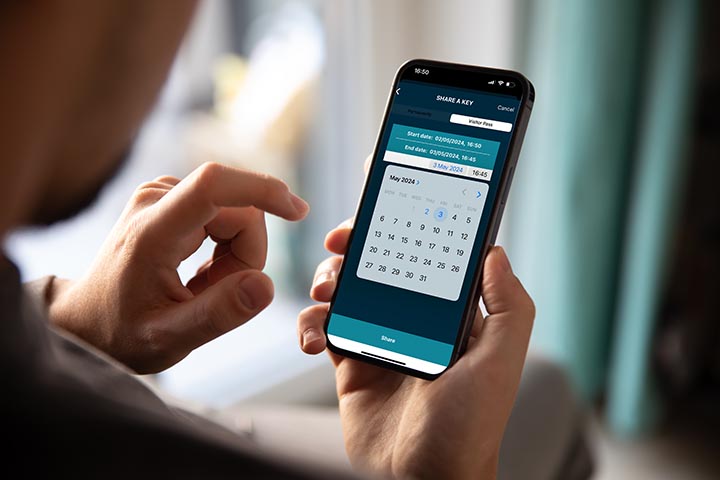
Automate your access operations with time sensitive mobile visitor credentials
End-users have the ability to manage readerless mobile access credentials for tenants, employees and visitors from anywhere, at any time, via a desktop, tablet or smartphone.
Transition users to NIST cyber secure mobile access credentials at your own pace
Sentry Interactive’s NFC mobile access credentials are engineered for comprehensive security. We are the only mobile credential SDK provider to follow NIST compliant standards by using the smartphone as the reader. Military-grade encryption protects user access data in the cloud, while audit logging and privacy regulation compliance further secure the data.




Embrace the fastest route to flexible mobile credentials
Extend the life of your access control systems and provide the choice of secure NFC mobile credentials to automate operations and optimize user experience.
Connect with a member of our team within 24 hours.
Get a system audit for integration.
Deploy and activate mobile credentials within days.

